Malicious ads push Lumma infostealer via fake CAPTCHA pages

A large-scale malvertising campaign distributed the Lumma Stealer info-stealing malware through fake CAPTCHA verification pages that prompt users to run PowerShell commands to verify they are not a bot.
The campaign leveraged the Monetag ad network to propagate over one million ad impressions daily across three thousand websites.
The malicious operation, dubbed “DeceptionAds” by Guardio Labs and Infoblox researchers, is believed to be conducted by the threat actor known as “Vane Viper.”
Evolving the ClickFix tactic
DeceptionAds can be seen as a newer and more dangerous variant of the “ClickFix” attacks, where victims are tricked into running malicious PowerShell commands on their machine, infecting themselves with malware.
ClickFix actors have employed phishing emails, fake CAPTCHA pages on pirate software sites, malicious Facebook pages, and even GitHub issues redirecting users to dangerous landing pages.
What GuardioLabs discovered is different from previous operations as it utilizes large-scale advertising on a legitimate ad network to take unsuspecting users casually browsing the web directly to fake CAPTCHA pages.
Specifically, the threat actors use the Monetag ad network to serve pop-up ads promoting fake offers, downloads, or services, that generally appeal to the audience of the host sites, typically pirate streaming and software platforms.

Source: GuardioLabs
Once the victim clicks on the ad, obfuscated code checks whether they are an actual person and, if validated, redirects the visitor to a fake CAPTCHA page through the BeMob cloaking service.
Although BeMob is used for legitimate purposes like ad performance tracking, in “Deception Ads,” it’s used solely for evasion.
“By supplying a benign BeMob URL to Monetag’s ad management system instead of the direct fake captcha page, the attackers leveraged BeMob’s reputation, complicating Monetag’s content moderation efforts,” explains Nati Tal, head of Guardio Labs.
.jpg)
Source: GuardioLabs
The CAPTCHA page includes a JavaScript snippet that silently copies a malicious PowerShell one-line command to the user’s clipboard without them realizing it.
Next, the page provides instructions to the victim on how to paste the “CAPTCHA solution” into the Windows Run dialog and execute it. This step runs the PowerShell command, which downloads Lumma Stealer from a remote server and executes it on the victim’s device.

Source: GuardioLabs
Lumma Stealer is an advanced information-stealing malware that steals cookies, credentials, passwords, credit cards, and browsing history from Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium browsers.
The malware can also steal cryptocurrency wallets, private keys, and text files likely to contain sensitive information, such as those named seed.txt, pass.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, words, wallet.txt, *.txt, and *.pdf.
This data is collected into an archive and sent back to the attacker, where they can use the information in further attacks or sell it on cybercrime marketplaces.
GuardioLabs reported the large-scale abuse to both Monetag and BeMob. The first responded by removing 200 accounts used by the threat actor in eight days, while the latter acted to stop the campaign in four days.
Although this effectively disrupted the malicious operation, GuardioLabs observed a resurgence on December 11, indicating that the threat actors attempted to resume operations through a different ad network.
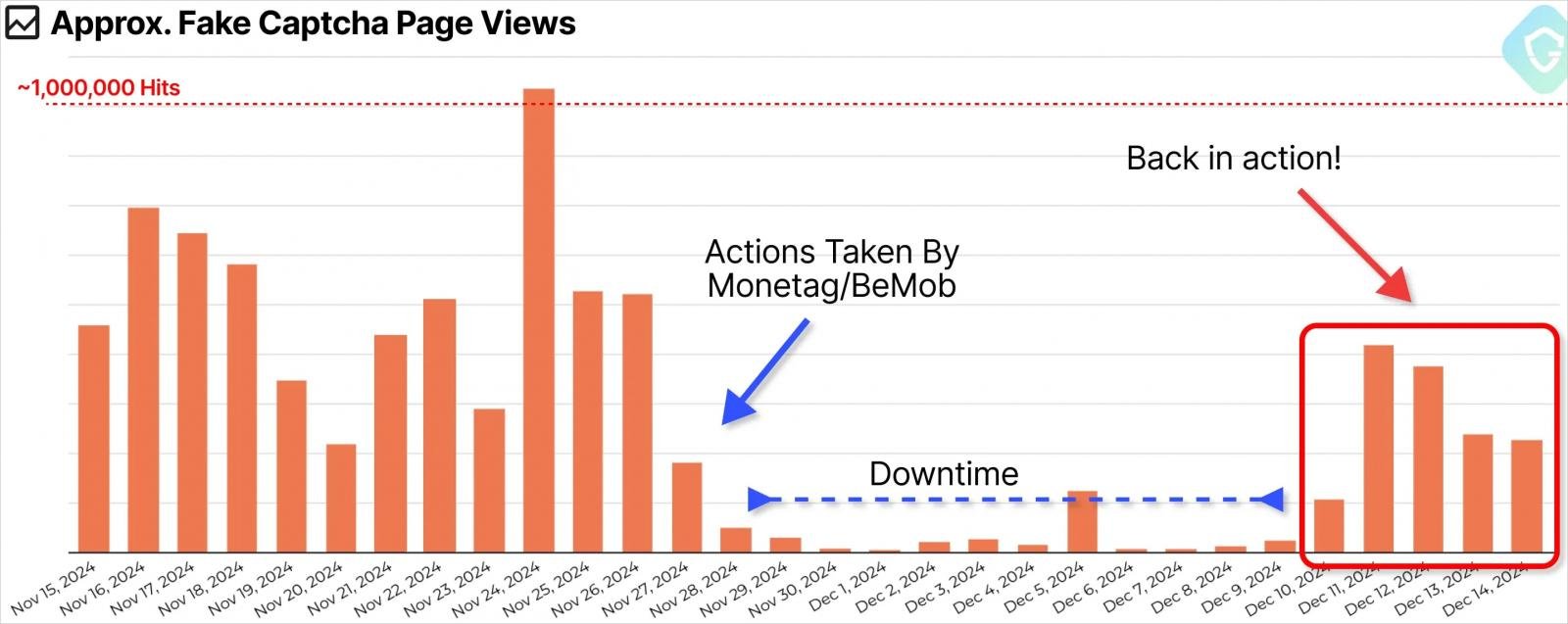
Source: GuardioLabs
Infostealer campaigns have become a massive global operation over the past year and can be devastating for users and organizations, leading to financial fraud, privacy risks, data breaches, and full-blown ransomware attacks.
In May, threat actors used credentials stolen by infostealers to conduct the massive SnowFlake account breaches, which impacted numerous companies, including Ticketmaster, AT&T, and Advance Auto Parts.
To stay clear from infostealer infections, do not ever execute any commands prompted by websites, especially those pretending to be fixes or captchas.
Also, using pirated software or illegal streaming sites increases the likelihood of such infections, as ad networks serving them have a more lax policy, and the site owners mostly care about temporarily monetizing their space and traffic rather than building a reputation for trustworthiness.
Source link